U.S. cyber security firm FireEye raised the alarm on Wednesday over a North Korean group that it says has stolen hundreds of millions of dollars by infiltrating the computer systems of banks around the world.
Since 2014, through highly sophisticated and destructive attacks that have spanned at least 11 countries, the North Korean hacking group has raked in at least $100 million. The report says the group is still operating and poses “an active global threat.”
The North Korean hacking group dubbed APT38 by the U.S. security firm FireEye says “the group is a large, prolific operation with extensive resources.” Another report had attributed the group as agents of the Reconnaissance General Bureau (or RGB), which is headquartered in Pyongyang. This is North Korea’s equivalent to the CIA.
The report points to the beginning of these hacking efforts around the time the U.S. and other countries clamped strangling sanctions on North Korea which led to a dwindling of state revenues. North Korea then turned to its military state hacking divisions for help in bringing in funds from external sources through unorthodox methods.
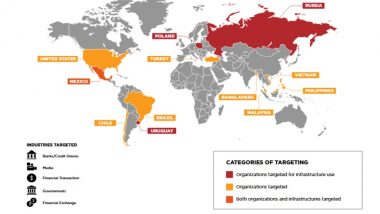
These methods relied on hacking banks, financial institutions, and cryptocurrency exchanges. The geography didn't matter, and no area was safe from APT38 hackers, according to FireEye, which reported smaller hacks all over the world, in countries such as Poland, Malaysia, Vietnam, and others.
Modus Operandi
The report describes the North Korean group’s method saying APT38 traditionally functions via malware that puts false transactions into the Society for Worldwide Interbank Financial Telecommunication (SWIFT), a system used for bank money transfers. The group then transfer funds to banks around the world, delete the evidence, and launder the money.
“APT38 is unique in that it is not afraid to aggressively destroy evidence or victim networks as part of its operations,” FireEye stated in its report, adding that the group is “active and dangerous.”
The Report
FireEye, which is staffed with a roster of former military and law-enforcement cyberexperts, conducted malware analysis for a criminal indictment by the U.S. Justice Department last month against Park Jin Hyok, the first time a hacker said to be from North Korea has faced U.S. criminal charges.
FireEye's "APT38: Un-usual Suspects" report details a timeline of past hacks and important milestones in the group's evolution.
- February 2014 - Start of first known operation by APT38
- December 2015 - Attempted heist at TPBank
- January 2016 - APT38 is engaged in compromises at multiple international banks concurrently
- February 2016 - Heist at Bangladesh Bank (intrusion via SWIFT inter-banking system)
- October 2016 - Reported beginning of APT38 watering hole attacks orchestrated on government and media sites
- March 2017 - SWIFT bans all North Korean banks under UN sanctions from access
- September 2017 - Several Chinese banks restrict financial activities of North Korean individuals and entities
- October 2017 - Heist at Far Eastern International Bank in Taiwan (ATM cash-out scheme)
- January 2018 - Attempted heist at Bancomext in Mexico
- May 2018 - Heist at Banco de Chile
APT38’s largest heist, says AP, targeted the central bank of Bangladesh in February 2016, when the group stole $81 million by wiring the money to bank accounts associated with fake identities in the Philippines. In all, they’ve attempted to steal $1.1 billion.
(The above story first appeared on LatestLY on Oct 04, 2018 02:11 AM IST. For more news and updates on politics, world, sports, entertainment and lifestyle, log on to our website latestly.com).












 Quickly
Quickly